Samsung starts a new race of 'multi-core', how not to forget the ID, the director of security is king, and the top management is no longer cool, and other news!

The world's first compact action glasses 360 ° ORBI Prime
The amazing object was created by the designers of the Socionext company, located in the city of Kanagawa (Japan).

We are all used to the fact that a 360 ° action camera is a pretty big device. But the Japanese decided it was time for the next step and presented the world with the innovative ORBI Prime sports glasses. This gadget is equipped with four 1080p cameras, a 1230 mAh battery, a wireless WiFi module, an electronic image stabilizer and multi-layer lenses with many filters and protective coatings:
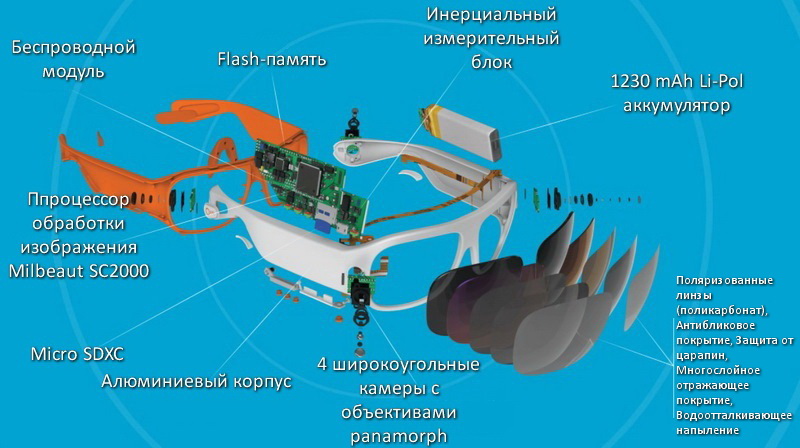
The system is based on the new Milbeaut SC2000 image processor. Its design features are unknown, but it processes four input video signals simultaneously in high bitrate 1080p quality. The proprietary software stitches four images into one and you get a full-fledged 360 ° video of good quality (it is recommended to watch it on a PC, not every smartphone will 'pull' such a 360 ° video):
Miracle glasses are available on pre-order, they want 399 US dollars for them and that's very little for such a thing.
Interaction with glasses is carried out through a proprietary application for a smartphone (via WiFi), and special emphasis is placed on 'sharing' the captured video in social networks.

These glasses completely free the hands of streamers, tourists, fishermen, security guards and anyone else who needs to capture the surrounding space. Remember 'Ide !!!'? Imagine how deep it would be to plunge into the atmosphere if the whole process were filmed through the eyes of a fisherman in 360 ° mode? And if you still wear VR glasses? All around the water surface and quiet, seagulls scream in the sky and suddenly a weighty ide is in your hand! So you need to rest, watching the summer 360 ° rollers on long winter evenings.
Samsung introduced a new chipset for smartphones Exynos 9810
According to the Korean giant, when developing the Exynos 9810, special attention was paid to improving the device's face unlock function. This was achieved by hardware processing of the 'face depth' and scanning it to build a 3D model. In addition, the chipset has undergone deep machine learning to recognize objects and faces in photographs.
CPU

The CPU is represented by two clusters of four cores each, with a maximum operating frequency of up to 2.9 GHz. The cores of the 'powerful' cluster at Samsung are called 'Custom CPU'. This name most likely hides ARM Cortex A73 cores, but time will tell. The second cluster for day-to-day operation is represented by Cortex A-55 cores. Kernels of this type appear for the first time on the scene and what they are is not yet clear, we will wait for tests and then draw conclusions. The chipset is made according to the second generation 10nm FinFET process technology, which provides a performance increase of at least 40% compared to its predecessors, as well as a decrease in power consumption.
GPU

Traditionally for Samsung Exynos, ARM development acts as a graphics subsystem, namely Mali G72 MP18 (Bifrost). This is a video chip for high-end devices, designed for high performance with extremely low power consumption. Up to 20% performance gain is promised over predecessors. At the same time, it is not specified with which ones, as always. Separately, I would like to note the hardware support for the VP9 codec, which will allow you to easily reproduce high-quality 360 ° video, and when using a smartphone and VR glasses, you will be fully immersed in virtual reality.
LTE

The integrated LTE modem allows you to download content at speeds up to 1.2 GB / s, and share information with friends at speeds up to 200 MB / s. It is noteworthy that the X6 signal aggregation gives hope for stable reception anywhere.
Photo
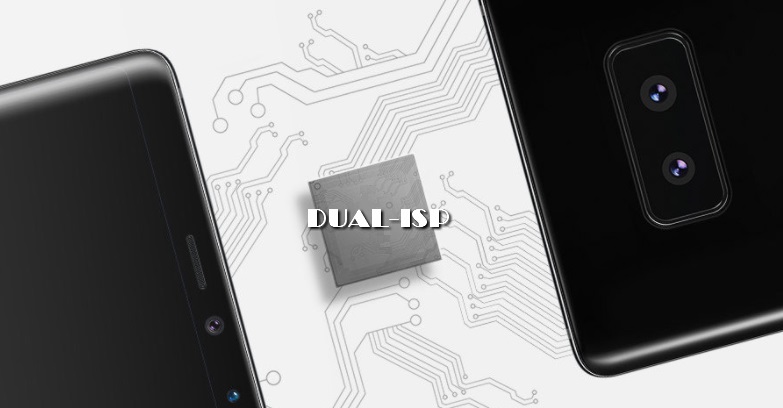
For photography (and related tasks), Exynos used a dual-core signaling ISP processor that can serve up to 4 optical sensors. One of the cores is designed for serious workloads, such as shooting 4K video at 120 frames per second, while the other, energy efficient, will save power during daily use. In addition, autofocus and post-processing of photography, face beautification, noise reduction, etc. have been significantly improved, and the 'new' is the promise of better quality in shooting areas out of focus.
As you can see, the race of “multi-core” has moved into a new quality and now signal processors, which were originally created to solve one specific problem, compete in it.
From LED to microLED
There are many types of LCDs on the market for mobile devices, ranging from the outdated TFT-IPS to the advanced Samsung AMOLED.

At this point in time, they are all produced by similar methods, with separate deposition of chips and illumination, data transmission lines and power elements on the substrate. This is the main reason for the limitation, which all manufacturers of matrixes for mobile devices have run into, unable to further increase the screen resolution while maintaining a small diagonal. But it looks like there is a way out.

Plessey Semiconductor is actively working on the ability to print the entire matrix on a single silicon substrate and using the same process technology for all components. The technology, long known as GaN-on-Silicon (gallium nitride on silicon), was previously used in the manufacture of trace elements for D-class car acoustics, blue LEDs and more. CTO Dr Keith Strickland explains the capabilities of the new dies:
“Gan-on-Silicon is the only technology that makes sense in terms of scalability and performance. It offers better thermal conductivity than sapphire matrices and higher brightness than OLED. This is exactly the technology that can realize both high resolution and brightness in a display.
The company calls its new monolithic displays microLED and is waiting for orders from large manufacturers. At least this is the conclusion that can be drawn after the statement of Michael LeGoff, CEO of the company:
“As a pioneer in the microLED monolithic display market, we will share our expertise and provide access to our proven turnkey solution, allowing manufacturers to scale up the development and production of microLED displays to meet these emerging challenges.
We can only imagine what size such screens can be. As a starting point, let's take a standard version of manufacturing a silicon wafer (using the example of a company Intel):

It turns out that on old foundry equipment it is quite possible to produce a base for monolithic dies with a diagonal of up to 8 ″ (offhand). It's worth noting that this technology is another step towards a fully monolithic smartphone.
Semiconductor Engineering has brought together leading electronics developers. What did you discuss?
It does not happen so often in the world that the world's leading experts in electronics and nearby things gather in one place. Therefore, it was impossible to pass by such an event in any way. Purely utilitarian issues of information security were discussed, among the participants:
– Mark Schaeffer is Senior Product Safety Manager at Renesas Electronics.
– Haydn Povey is the CTO of Secure Thingz.
– Marc Canel is the vice president of security systems and technologies for ARM.
– Richard Hayton – CTO, Trustonic.
– Anders Holmberg – Director of Corporate Development at IAR Systems.
– Ed Sperling – host and journalist for Semiconductor Engineerimg.

(Left to right: Anders Holmberg, Marc Canel, Mark Schaeffer, Haydn Povey, Richard Hayton.)
Below are key excerpts from their dialogue.
Ed Sperling (presenter):
One of the major security concerns is the complexity of systems and devices. How do we solve this?
Haydn Povey:
Complexity is a serious problem for everyone. Whether you are building a power plant or a machine, it is made up of layers and layers of components and systems. A control system must be built into all of this from the very beginning. The component ID must be entered before the component is manufactured. We need to control each component throughout the life of the system and be able to refer to it at any time. We need to be able to manage subsystems, integrate them, and integrate security into them. But there are so many pieces, so many pieces of complex code, that it's a real challenge to manage it all. The solution is to simplify. You must control, update, and certify components. Certification is a key part of this. If you cannot formally prove that the system is correct, then it is probably wrong. And you can only do this at a small level, be it a microcontroller or a TEE (Trusted Execution Environment, protected area of the main processor) level.
Mark Canel:
Complexity is one aspect of the task. There is a hierarchy of technologies, starting with the physical IP, in which the key is embedded, which gives the main access right, right down to the applications and everything that happens between them. There is also complexity in the processes that load code and keys. One of the major problems is the lack of standardization in the IoT world (I told you! Approx. A.N.). There are vertical ecosystems, for example, in the automotive industry. But, if you log out of General Motors and go to Ford, then you will be faced with a different ecosystem, different rules and requirements. Lack of normalization and standardization complicates the situation, processes and technologies need to be standardized within the market.
Ed Sperling (presenter):
There is more, isn't there? What can you say about the fragmentation of the ecosystem (management and production systems, safety and technical requirements)?
Mark Schaeffer:
The complexity of ecosystems at all stages of production and operation exceeds the ability of most people to manage them. An excellent example is the Equifax hack (Equifax is an American credit bureau, hacked in the fall of 2017). The CEO argued that the blame rests with one person who has failed in his duties. This is absurd. Nobody checked and insured this 'key' person? And there were no other security mechanisms? And this is the CEO of the company! This is a big flop, and it happens across the spectrum. People are either not held accountable, or they cannot understand anything, it is so complicated.
Richard Hayton:
Understanding is the key part. We all say that security is good, but people do not understand what exactly they need to do. How do you know in a complex ecosystem if the other guys are doing the right thing? There are many people who develop a product in which safety is not what the product is designed for. Of course, this is what they should be doing. If no one brings them (the developers) to an account, and no one knows how to bring them to justice, because their secret IP address is not available to anyone, and if so, how do you know that a hack or leak occurred at all?
Mark Schaeffer:
This is true, and a good example is the TLS (Transport Layer Security, which replaced SSL) stack. People say they have a TLS stack and you can trust the vendor. But provisioning and storing keys is beyond what the TLS provider is responsible for. And most people don't even get it.
Haydn Povey:
Absolutely. There should be a requirement across our entire industry to publish security best practices. Most companies would like to do the right thing. We all want products that stand firm and we want to improve the usability of those products. However, many people do not know where to start in order to ensure safety. I serve on the executive steering committee of the IoT (Internet of Things) Security Foundation. And we are trying to publish best practices. This is not a direct action guide like, 'This is what you should do.' This is a set of best practices with a checklist that you can go through and determine the level of your products' compliance with our requirements. Fragmentation of a security problem is so difficult that you can spend all your money and not be sure whether it is safe or not. But at least if you have a set of best practices that can be applied to your product, then you can at least indicate that you went through the process.
Anders Holmberg:
Let's take a look at all of this from a software perspective. You mentioned the Equifax credit bureau hack. Several years ago, we witnessed a hacked SSL stack, and last year the Mirai attacks (a worm and botnet created by a software vulnerability in IoT devices). All of these high-profile stories are caused by software problems. Because even if you have hardware access rights, you still need to get access rights from the software. All these loud hacks are caused by poor quality software.
Ed Sperling (presenter):
Who is responsible for this? Programmers? Hardware part? OEM?
Mark Canel:
This is a very good question, and it is what drives the introduction of security into some systems. Nobody wants to pay for security. Security is added when there are regulatory requirements, or when its absence poses a threat to the company's reputation. And even then, we see what can happen with Equifax. So industries that look bad in terms of security, other than the government and the military, start paying for security. These include Hollywood studios and the entertainment industry who are concerned about protecting their content, and mobile network operators who are protecting their customers' data. That is why secure elements are the basis for SIM cards. If you look at these companies closely, you will see the same security service provider, different in each industry. This security provider monitors the entire delivery chain or production process, provides the company with the necessary tools and recommendations. This supplier then creates distributors or OEMs and takes full responsibility on them. Despite all this, you still need a person with muscles to ensure that the entire system functions properly.
Haydn Povey:
If we take the manufacturers of products for airlines, then for them safety means the correct manufacture of a part, according to a certain standard, in a certain way and using the right metal. The right process ensures the right quality. They manage them like statistical assets. This is also true for digital assets. You can see this happening in the automotive industry 'for safety reasons'. This also happens in medicine. And this happens in payment systems and banking services, because you can lose money without it. This approach will soon begin to influence the IoT industry as well. At some point, legal regulation will come, but it will be very specific to the industry.
Mark Schaeffer:
Instrument suppliers are probably the most knowledgeable about safety. They always talk about getting the keys straight from the factory. There are several differences between a measuring device and a medical device. The CEO knows that even hacking a banal electricity meter will directly affect the company's income. This is not a question of responsibility. They are losing money directly. Or take cell phones, which is a great example. The user has an incentive to hack their own device. You won't hack your pacemaker, but you will hack your phone. And if you look at who has this incentive, then make sure that even the CEO has it. If you think about the Equifax hack, there may have been dozens of people who knew about the security issues, but they had no desire or incentive to do anything about it. Even if the security of your company is under threat, but you are doing a great job and therefore everyone turns a blind eye to it, and the maximum that threatens you is dismissal, then where is the incentive to fight to improve security?
Ed Sperling (presenter):
If you do a really good hack, no one will notice?
Mark Schaeffer:
It's true.
Haydn Povey:
The head of security should be an information security specialist. This person should not be responsible for IT and processing of incoming data. He must be responsible for the security, confidentiality and management of the product produced by his company (in the Russian Federation, the opposite is true, note A.N.). He needs to manage the processes and ensure that the technical regulations are observed. Security has traditionally been viewed as part of a company's costs. It is not right. This is the core value for the next generation. It starts with making a transactional sale, selling the company's image and ends with monitoring the implementation of a long-term strategy for the development of the company. The requirements of the director of security apply to the entire top management and these people must take responsibility. The other side of the coin is that if the company is wrong, the top management gets a bullet. At the entrance to each enterprise, there is a CIO, CISO and CEO at the stand. They have a responsibility to take care of the company, shareholders and employees. This is the place a security service should be in an organization.
Instead of an afterword
The luminaries of electronic security and production have had a rather lengthy exchange of views. What conclusions can you come to in the end? Maybe to such:
- Everything can be hacked and a good hacker cannot be caught, because no one will notice the hack.
- Lack of standardization of electronics in the field of security leads to the constant emergence of new threats and vulnerabilities.
- Even in the dialogue of luminaries on a global scale, attempts are being made to shift all responsibility onto subcontractors.
- In the near future, in Western companies, the security director will take all power into his own hands, and the top management will turn into a consumable.
Do you think someday there will be order in the world of electronics? Will there be real tools to protect ordinary citizens from hackers? And why do we like hacking our own smartphones so much?
