A short training course for the internet couch fighter. With slides and delivery Android – tools.

Image meritalk.com
The third world war is already taking place, and the main battlefield is in the information field of the planet. Along with open hostilities, such as cyber attacks on Iran's nuclear facilities, which have recently taken place, interventions are taking place in the holy of holies – to represent new generations of the world in which they live. This is, of course, about rewriting history and perverting basic human values. But if war has not been declared, then isn't the state's response too harsh?
Introductory
Each person is kind by nature and strives for justice, and what justice and kindness are, he learns from his parents and, further, from the members of his environment respected by him. The source of infallible data, a kind of knight in white armor and on a white horse, was previously a TV. They blindly believed him, and the theses expressed from the screen were wonderful. As for our common Soviet Motherland, even taking into account the constant exaggeration of the successes of the political system and the underestimation of its shortcomings, we can say that the Soviet citizen brought up by television was full of dignity and full of bright hopes. It was only later, when he first sat behind the wheel of a dump truck or a milling machine, he noticed the glaring difference between the picture from the TV and the harsh reality. But the process of teaching moral values was already completed and therefore many unselfishly strove to realize the dream of a wonderful Soviet life. In the West, the same thing happened, with the only difference that money has always been at the head of the educational process. To live well, you need to have a lot of money, and rich people are the most respected members of society. Work a lot and honestly, then you will have a lot of money, and if you behave badly (break the laws), you will be sent to prison and you will not have money, you will be poor and despised by the whole society. In 1991, the war between the two ideologies ended with the victory of rough materialism, and the countries of the Soviet world adopted Western values. A little later it turned out that, unlike the previous values, the new ones are absolute only for the internal space of the state, and beyond its administrative boundary no one prevents a democratic state from acting on the basis of other values, for example, barbaric or imperialist. This is the answer to the question why after 1991 there was no general prosperity and the world did not become filled with rich and happy people. Despite the fact that the two largest ideological centers began to play on the same side, the competition between democracies turned out to be no less fierce than between ideological enemies, and capitalism is the main instigator of this movement. Unable to simply deploy troops and blackmail the survivors, large (and high-budget) states, in order to achieve the commercial interests of the largest taxpayers, begin information intervention, the ultimate goal of which is always to replace the government with a more accommodating one. Needless to say, the aggressor is not interested in the interests of ordinary citizens in an informationally occupied country? They are not spelled out in any way in its Constitution, and for these needs not a single coin will ever be allocated from the budget. After all, the goal of intervention is to make a profit for the budget, and not vice versa.
Objectives
The targets of an information strike are always competing enterprises (locally), as well as politicians and their family members (in general), who consistently pursue the sovereign policy of the state, avoiding external interference in its economic interests.

Image by ceoworld.biz
In the era of widespread digitalization, you will not find a single large enterprise whose production computers, accounting and HR database would have direct access to the global network. A direct cyber attack on such an enterprise, with the subsequent destruction of all data on its servers, can occur only after secretly and illegally changing the configuration of its internal network, which is problematic in our countries (there are guards at the entrance, there are literate IT specialists inside). The 'victim' enterprise may go to court and then the aggressor will not be in good luck, and the reputation losses are negatively monetized in one way or another. But if there is a political cover for the attack, for example, the “fight against evil” declared and recognized by the majority of interested parties, then the capitalist state's hands are untied, and it can do almost any lawlessness against competing enterprises in foreign territory. For example, to destroy a large aviation concern of another state, interfering with its own aviation concern, which generously feeds the budget.

The world's tabloids are filled with similar content. No one is embarrassed anymore that military information actions are being carried out without a declaration of war
In the case of politicians and their family members, powerful political parties and the will of the advanced population to resist, everything is somewhat more complicated. Modern methods of such an information attack, in my opinion, follow two scenarios.
- In the first case, compromising evidence is used against the leaders of the movement, they are forced into secret cooperation or public resignation in disgrace. The target of the information attack begins to work not for its own state, or it is replaced by an agreeable 'reformer'. A reformer who will destroy not individual enterprises, but entire industries. The first bell that a citizen should pay attention to is the presence of offshore accounts with those in power. You can't sit at a parliamentary meeting and not think about your millions if you are a millionaire and your money is held hostage abroad.
- The second method of suppression is the erasure of the historical memory of the entire population and the processing of critically under-saturated heads of the younger generation with information. As a result, the citizens of the attacked (!) State should have an inexplicable love (conditioned reflex) for the government of the attacking state.
On the first point, everything is clear, but on the second, I consider it necessary to chew a little and poke my nose into the world of animals for this. Despite the fact that a person imagines himself a free and independent being, he is not much different from other animals. In relation to him, the laws of inheritance from parents of successful qualities work, and an adult can be tamed and trained. And there is no doubt that in ideal laboratory conditions it will not be a problem to bring a person with a predetermined disposition to complex behavioral reflexes. The video below shows well how the individuality of an animal breaks down in just a few generations, how the 'enemy' becomes a 'friend' at the genetic level:
The only protection of an individual from such external influences is his memory of himself, the memory of events described by his ancestors and other members of his community (collective). It is memory that prevents him from taking sugar from an unfriendly hand. In the context of the study of information warfare and means of protection against it, the blow to memory is the most dangerous, and its results can be observed all over the world. The recent meeting of the countries, when they were former allies of Nazi Germany, on the occasion of the celebration of the victory over her, is a vivid evidence of this. How it works?
Imagine the conditional Seryozha, who in the club took away a glass of vodka from the conditional John. Everyone condemns Seryozha, because this is an absolutely unseemly act, the girls refuse to dance with him, and the bar – to serve. Further investigation would show that prior to these events, John borrowed money from Sergei and did not return it in a rude, obscene manner. But no one will conduct such an investigation, because the girls are not interested in this, and it is more convenient for the bartender to think in simple categories, without going into details. And now an act of historical justice has been turned into a crime, and the real victim has become an aggressor against whom sanctions, economic blockade and censure have been introduced. A reverent and thrifty attitude to the immutability of its history is the most reliable shield from the information blow.
Examples of information warfare in Runet
For me personally, the signs of information war became noticeable in 2010. It all started with watching a video on YouTube called 'Peter Pig Eat …'.

The video tells how the piglet Peter leaves Russia on a stolen tractor abroad. Due to the fact that this video can be viewed in two ways (depending on political beliefs and the level of intelligence), it can be considered both an appeal to young people to flee the country, and an open letter to the authorities, demanding to take care of the welfare of the population. Despite the fact that everyone understood it in their own way, a fair amount of noise was raised, the video quickly went viral and largely pushed the country's population towards migration. Now the informational feedback has gone from migrants in the form of a very inconvenient truth, but then the image of 'abroad' was still shining like a beautiful distant star, like an unlimited freebie, to get which you just need to come. I hope that the video will be reshomed and the piglet will arrive where the piglet is supposed to come – to the slaughterhouse.
Piglet, nevertheless, showed that in the information age it is very simple to use means of delivery of information (including destabilizing information) and anyone can do it, from patriots and their opponents to sexual perverts. The events 'after Peter the pig' can only be described as 'And it poured'.
Propaganda sites began to put Stalin and Hitler on a par, bloggers turned into politicians and began to relax on the ocean shore with money received from subscribers, and state organizations began to have headaches (and continues to be). Objectively, a person is a social animal, which means that three can almost always convince one of anything, and a crowd can always. Why don't you think that you are one against everyone when you are sitting on the phone and reading another article, and then commenting on the material? You are the only one and the arguments of the majority act on you in the same way, as if the matter was taking place in an open field. You are protected physically (you will not be knocked with a fist for an opinion), but not psychologically, you can fight for a while, but you only have to give the slack once and the herd instinct will win. And only because of this, I do not agree with my own government, which is trying to block hostile information, which, if successful, will lead to the emergence of a kind of “society of consent” within the information field of the state. The world is arranged in such a way that individual freedom is realized only in the struggle, when members of one “society of agreeable” fight with other “societies of agreeable”, and stagnation inevitably causes degradation. A person will not be able to exercise his right to choose if he has nothing to choose from, and then he will forget that he had this right. Let's call this the doctrine of limited information conflicts. And, of course, a person (if he is healthy) cannot but want to know what others are saying about him, and the further from him the reaction occurs, the more interesting he is.
Legal justification for blocking and protecting Runet
For us, as consumers of network traffic, it is important to know only one thing: All prohibitions and blockings are imposed on Internet providers and specific information resources, and not on citizens. If a citizen bypasses the provider enters a prohibited (blocked) resource, then he does not violate a single law. And let's finish all speculation on this topic.

Roskomnadzor-chan. Image Kanobu.ru
The reaction of children to constantly forbidding adults is interesting. Roskomnadzor was immediately memenized, got a nice girlish appearance and became a frequenter of cosplays.
The idea of the state about the means of saving the people against its will was already deeply rooted in youth, as unacceptable. It's just a fact.
Practice bypass
So, Roskomnadzor is installing equipment that will ensure the country's information security using DPI technology. The Deep Packet Inspection technology itself (deep packet inspection) appeared to protect the end consumer device, and it was supposed to be mounted in a room or industrial router. No one could even think about its application in relation to an entire state, I am talking about our state, and not about another.
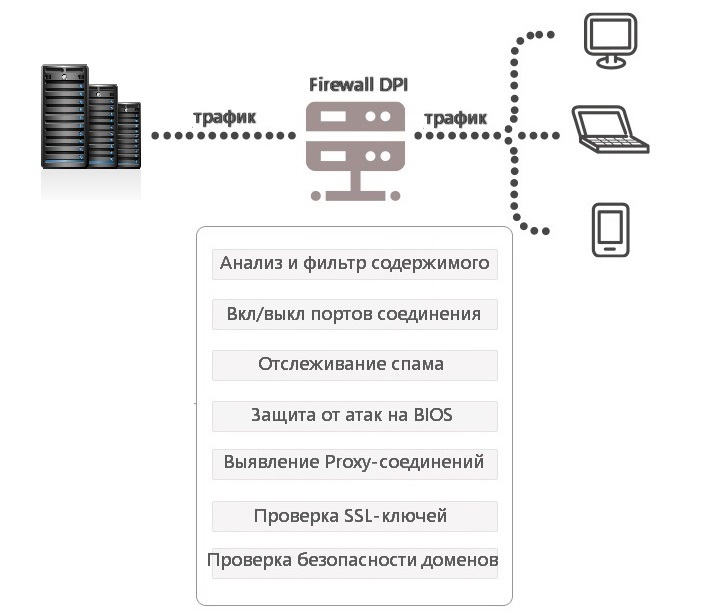
The most dubious thing about all this is that the 'great firewall' can work both ways, reading (in constant mode) the contents of not only incoming packets of information, but also outgoing ones. I don’t remember that we were deprived of the right to confidentiality of correspondence, and you guys? What is happening is called legal nihilism, at least until there is open technical information about this equipment (name and photos), convincing evidence of the impossibility of reading the emails of ordinary citizens and the correspondence of private enterprises with their foreign offices. Nevertheless, these same citizens, without breaking the law, are looking for ways to bypass the blockages, both existing and prospective. AMR has previously talked about Tor networks, paid VPN connections, and other tools. But the Psiphon system can be considered the unconditional discovery of the late summer and autumn of 2019.

Despite the fact that the Psiphon Inc company has existed since 2007, a more or less working application for Android appeared with them only now, in version 2.4.4. The current application breaks a secure tunnel on the network, is much faster than Tor networks in free mode, and is available for operating systems Windows, Android and iOS. The installation takes place as standard, with the first launch quite logical requests for permissions pop up. If you agree with everything, then nothing terrible happens:
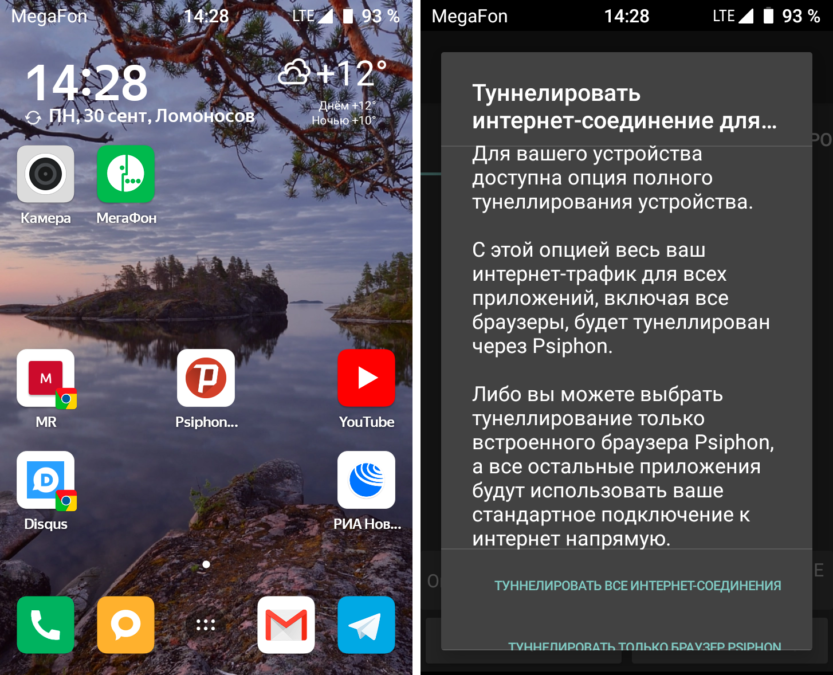
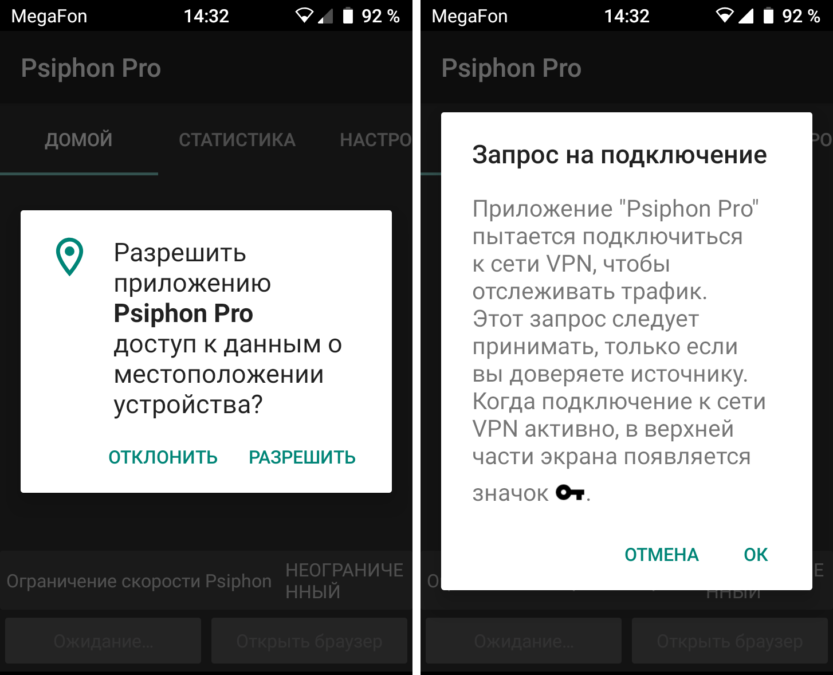
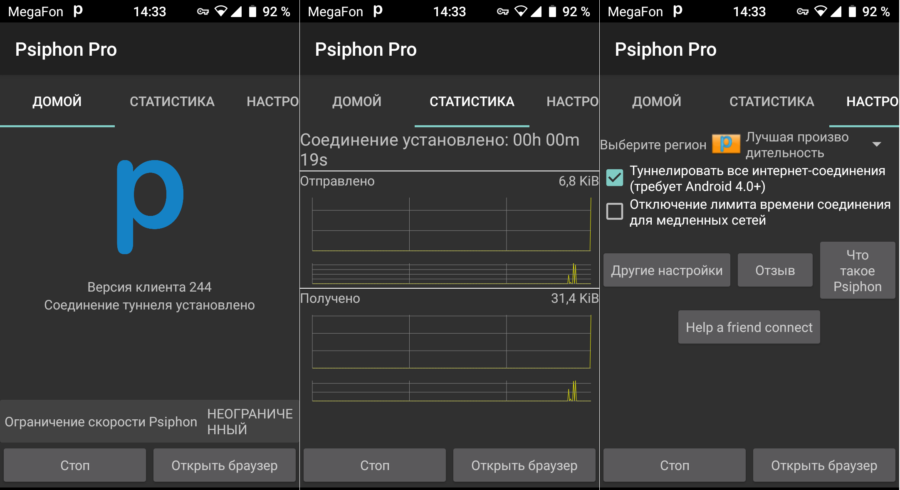
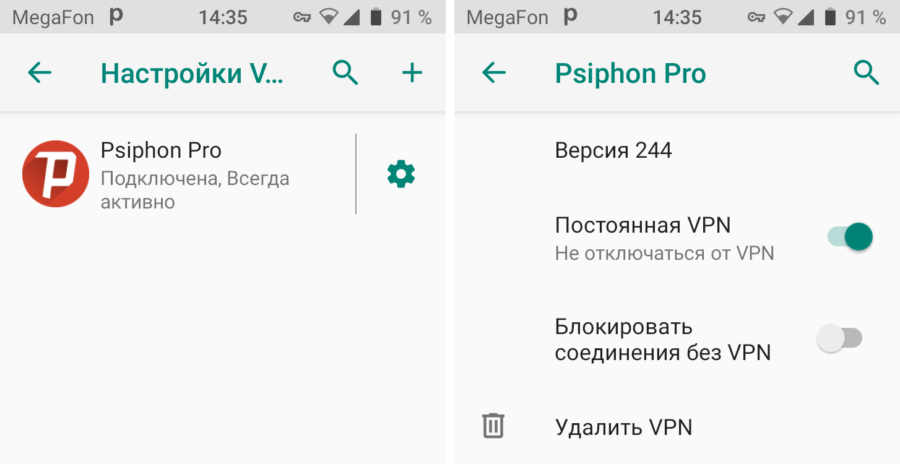
Psiphon can be used as a Firewall and disable Internet access for any application. This can be achieved by setting the appropriate settings in the smartphone menu and application. The screenshot shows the standard settings menu Android 9 'VPN'.

A running Psiphon application displays a 'P' icon in the status bar, but you can really turn it off only from the application itself, from the notification area it will not work. At the first start, depending on the version Android and access rights, the following options are allowed – either provide a tunnel only for the browser, or for all connections. In the future, in the program settings, you can disable applications that do not need a tunnel. Based on the results of the application, we can say that there are no problems with access to Ukrainian sites blocked for Russians with dubious but terribly interesting information, to pirate servers and some overseas resources. Failure befell only in the case of the long-suffering Rutor.org server, to which it was not possible to access either the very first address (they say that it was completely deleted), or the second (new-rutor.org), or with the Megafon LTE connection. nor via Wi-Fi from the Rostelecom provider.
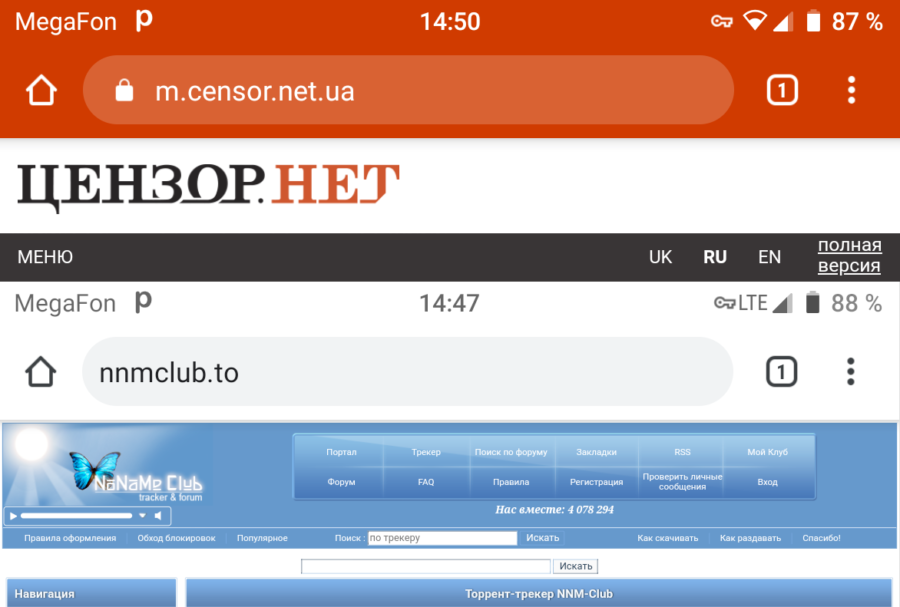

Psyphon's VPN connection slows down the download speed quite a bit.
Oddly enough, in Windows, when using the Psiphon desktop application, the Rostelecom stub on Rutor was successfully overcome.
Instead of a conclusion
The most interesting question that arises after studying DPI technology is that there are no uniform standards for network equipment that implements the functions of reading traffic content. Each such device is unique, as are the specific software and hardware methods that it uses. What exactly is inside the boxes that Roskomnadzor is testing in the Urals, and what exactly this equipment will do, is known only to a narrow circle of specialists involved. And we just have to look for ways to bypass the blocking of sites and avoid illegal checks of the content of our information packages in order to freely receive and distribute information by all legal means. Friends, what means do you use for this?
