We communicate with a specialist of the company …

Hello everyone! Today we bring to your attention a short interview with Alexander Ivanyuk, director of product and technological positioning at Acronis, whose products I have repeatedly written about on the pages of MR / AMR. During the conversation, we will discuss the current situation with the increased activity of various ransomware programs and ask an expert for advice.

Hello! Thank you very much for agreeing to communicate within the framework of our not so constant, but interesting for me as the author of the column and the user. Tell us, how long have you been with the company and what areas are you responsible for?
Good afternoon, Ilya. I have been with Acronis for about a year and a half and am responsible for positioning the company's products to different markets and audiences. At the same time, I make an important connection between the development department and the marketing department, because it is often difficult for developers and marketers to understand each other, since their goals and objectives are different and they think in different planes. In addition, I help develop technology partnerships and, to the best of my ability, participate in the launch of a number of the company's products to market, and also take on the role of an evangelist on related topics, such as threats and ransomware.
Readers of our resource are already familiar with some Acronis products. The company develops solutions for comprehensive protection of user data, including from ransomware.
What is the reason for the rise in ransomware attacks and the increased damage they inflict on users around the world?
Ransomware is perhaps the fastest way to get money from the user, that is, to monetize malware, be it specially designed or leased. Recently, for decrypting data, all attackers have been demanding a ransom in bitcoins or other anonymous cryptocurrency. This makes it easier for them to get it – there is no need to take any unnecessary actions in order for the money to 'enter your hands'. Cybercriminals understand that people are willing to pay the ransom because their devices often lack adequate protection.
The fact is that users do not know enough how to protect their data and devices from malicious attacks, and they, in turn, use this, or are cybercriminals constantly improving the ransomware code every time?
In fact, both. Of course, the root cause is a lack of knowledge of IT security and rules of safe online behavior. This is followed by the problem of the lack of security software on the user's device and, finally, the factor that cybercriminals are constantly looking for ways to bypass anti-virus and other protections, find new vulnerabilities in the operating system and third-party software, or invent new social engineering schemes, which are still works excellently and without which cybercriminals cannot do now.
As for updating the code, say, within the same malware family – of course, this happens all the time in order to bring down the detection of anti-virus software.
As a user, have you encountered such ransomware?
I know how to behave on the Internet and what threats you can face, of course, I use security software on my devices, including a backup solution. So infections, and even more so the loss of data, passed me. But I can say that, of course, I received malicious emails (and this is the most common method of infection today), which could easily contain attachments or links to ransomware.
Please provide your recommendations for protecting your data from ransomware attacks. What are the basic steps each user should take?
I will give some simple tips:
- You need to have antivirus protection and a secure backup on your computer, such as Acronis Ransomware Protection, Acronis True Image 2018 or Backup 12.5 with Active Protection technology that detects ransomware, instantly blocks them and restores encrypted files. In this way, you will avoid downtime and interruptions in work.
- You need to regularly update your operating system and third-party software. But it is important to remember that third-party software is not updated on third-party sites. It either updates itself automatically (this function is now available in almost all popular software), or it needs to be updated from the website of the manufacturer of this software.
- You cannot open suspicious email attachments and click on links sent, especially from unknown senders.
- You need to use strong passwords that are different for each service.
In a recent press release, Acronis just talked about the new Acronis Ransomware Protection solution aimed at protecting users from all kinds of ransomware. Share with our readers the details about the new product?
Acronis Ransomware Protection, which includes machine learning and artificial intelligence (AI), provides an additional layer of protection and can work in conjunction with other data protection solutions already installed on the corresponding device, such as antivirus and backup software.
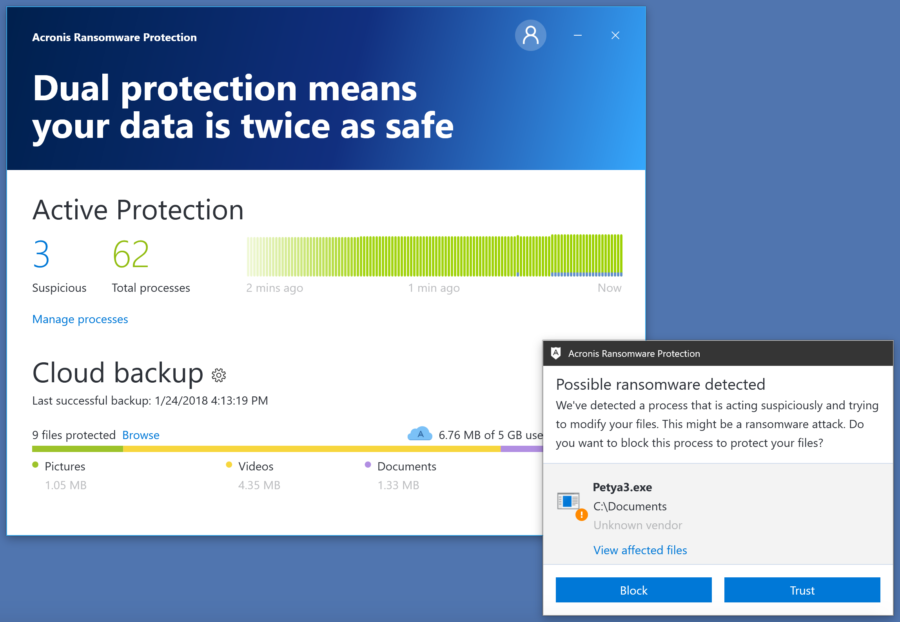
Our solution is based on our own unique technology Acronis Active Protection. It is independently tested to be the most effective and reliable anti-ransomware technology on the market. The technology monitors processes and applications in real time, which automatically detects and repels attacks that other solutions fail to cope with. In the event of a ransomware attack, Acronis Ransomware Protection blocks the malicious process and notifies the user via a pop-up message. If any files are damaged during an attack, the Acronis solution will help users recover these data in seconds.
Together with Acronis Ransomware Protection, users get 5 GB of free cloud storage to back up and protect important data not only from malware, but also from hardware failures, natural disasters and other events that cause data loss.
It is also worth noting that Acronis Ransomware Protection does not require any effort from users to install, but it will help to avoid many problems. The solution takes only 20 MB and practically does not require system resources, so it can work in the background without affecting the performance of the protected system in any way.
Our solution uses unique behavioral heuristics enhanced by machine learning models. Models are generated by analyzing hundreds of thousands of malicious and legitimate processes in a dedicated Acronis cloud infrastructure. They are embedded directly into the Acronis Ransomware Protection installation package, which allows you to protect system data autonomously, without a permanent connection to the Internet. Powered by artificial intelligence, this AI-powered feature effectively tackles all types of ransomware, including zero-day attacks that go undetected by signature-based solutions.
It turns out that this solution is like Acronis Active Protection, but a separate product?
This statement is not entirely true. In addition to anti-ransomware technologies, the product also includes backup functionality, which means it is a comprehensive, multi-layered data protection solution that we provide for free.
What is the superiority of your solution over the products of other companies?
Acronis develops data protection solutions. Consequently, the Acronis Active Protection technology at the heart of our products protects the data, not the system. Also, our behavioral heuristics track what happens to the data, not the operating system. The fundamental difference, which is important for the user, is that the antivirus product may not recover files or partially recover if something happens to them, because the antivirus has another task – to get rid of the threat. And we will recover data, moreover, quickly and without size limitation. While no antivirus can recover a file of several tens of megabytes.
Our focus on data also allows us to achieve good performance. And since antiviruses monitor the entire system, the problem of performance and the so-called user experience in this case is much more acute.
If you compare us with other backup solutions, then it is worth noting that they lack protection against ransomware and the low level of self-protection. That is, attackers in this case can turn off the client application on the Windows – computer or penetrate the process or registry and intercept access to the cloud. And then delete both local and cloud backup or encrypt. With Acronis Active Protection technology, this is simply not possible.
At this stage, Acronis Ransom Protection works only on the platform Windows. Are there plans to create similar products for other platforms?
Depending on the demand and the evolution of the ransomware situation in the market, we will make a decision to release a product for other operating systems. While the most attacked system is Windows, for others the level of threats is noticeably lower.
An inquisitive reader will probably wonder about product monetization. How do you plan to monetize Acronis Ransomware Protection solution?
The cost of providing the service is planned to be compensated for by users who buy solutions with advanced functionality and capabilities after they have gained experience in using a free solution.
Well, everything looks pretty convincing, especially in the context of the lack of influence on the speed of the system. I will definitely download and try the product in action.
Let me have a few more personal questions. What gadgets do you use on a regular basis? What do you like most from technologies, maybe you are waiting for some kind of announcement?
One of my hobbies is video game consoles, which I follow. As for technology, I have a rather global interest. I'd like to see a fundamental breakthrough – quantum or bimolecular computers available to ordinary home users.
What is the biggest professional challenge for you at the moment?
Organize your working day in such a way as to be in time for everything. There are a lot of interesting tasks and new information, and there are only 24 hours in a day.
What would you be doing if not for your current employment?
I would start making video games.
~
Thanks again to Alexander for taking the time, even if the conversation turned out to be not as detailed as we would have liked, nevertheless, it was interesting. But, as is the custom, according to a tradition beyond my control, the articles in this section are as spontaneous and unexpected as possible, as happened this time. I will try to introduce some planning in this regard, I am already preparing material for the next interview. You can leave your questions to Alexander in the comments. See you soon on the pages of AMR!