A summary overview of relatively recently discovered malware samples for Android.

Despite active efforts by Google and OEMs to improve the security situation Android, the open nature of the OS, coupled with the curiosity and / or unwillingness of users to pay for applications, continues to put a spoke in their wheels. Moreover, the authors of such applications do not stand still, coming up with new schemes for involving unsuspecting users in their plan to enrich / obtain the necessary information or resources. You need to know the enemy by sight and be able to deal with him, since there are ways and they are not at all complicated. So, we get to know / remember.
GhostPush, Shedun, Kemoge and Shuanet
We will talk about a family of malicious software of four representatives, united by almost identical program code, similar effects on devices and exploits used (Memexploit, Framaroot, ExynosAbuse). According to Lookout, there are up to 20,000 infected apps outside of Google Play, which mostly affect users in Germany, Iran, Russia, India, Jamaica, Sudan and Brazil.
A new type of malware, discovered last September by Cheetah Mobile, was dubbed GhostPush (ghost) due to its ability to spread quickly and stealthily across devices. About 900,000 smartphones and tablets based on Android all over the world were infected, which cannot be called a special case. The Trojan externally disguises itself as popular programs (Calculator, Smart Touch, Assistive Touch, Talking Tom 3, Easy Locker, Privacy Lock, etc.) and, after being protected, can even get into Google Play or Amazon Store. Once on a device, GhostPush gains full control over the device at the root level. After that, hackers can install adware applications on the device without the owner's knowledge, and they are not free at all: according to Cheetah Mobile, the income from such a scheme could be up to four million dollars a day.
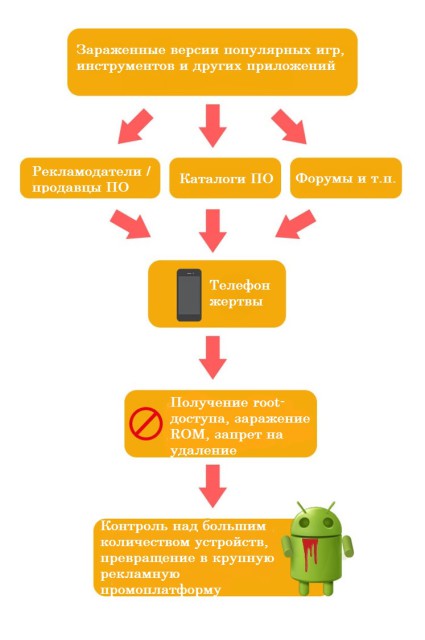
Interestingly, GhostPush (like the next two types of malware) cannot be removed from the device, even a full factory reset does not help. So the owner of the infected device can only buy a new one. However, not everything is so gloomy: the 'discoverers' of GhostPush have posted an application on Google Play that warns the user of a possible threat when downloading an infected application. We'll come back to ways to protect against this kind of malware.

Shedun is in many ways similar to the previous type of software: the same hidden nature of distribution, similar to access to system functions of the device. However, this type of malicious software is distinguished by a more subtle approach to deceiving the user: it not only downloads applications unnecessary for the user, but also installs them with access to special features – a number of settings for alternative methods of controlling the device. Shedun takes advantage of this standard feature, not its vulnerability. After gaining access to accessibility features, Shedun will be able to read the text that appears on the screen, determine that it is prompted to install software, scroll through the list of permissions, and agree to install without user intervention. This ensures the installation and execution of advertised applications, which in turn increases the profits of fraudsters. This class of malware is rapidly evolving and leaves the user no choice, forcing him to forcibly use this or that application and contribute to the enrichment of cyber criminals.

Shuanet is also very similar to previous versions of Trojans, except that in some cases it leaves the original applications intact and fully functional, making it difficult to detect. This variety is disguised as clients of popular instant messengers and social networks, as well as the Candy Crush game. After installation, Shuanet, like the already mentioned Trojans, automatically gets superuser rights, downloads the necessary software, and transfers the downloaded malicious application to the system partition, preventing its removal. Shuanet is not found on Google Play, but you still need to keep an eye on what you install on your device.
Kemoge, also known as ShiftyBug, has probably made the biggest splash of this 'family'. It is based on the same idea: an ad app. disguised as one of the popular products, getting root access, managing the device for the purpose of getting rich. Kemoge uses 8 exploits for its own purposes, which are aimed at breaking the protection and most of which attack Samsung devices. Malware runs even on rooted devices and often escapes detection by varying the time it takes to access the aps.kemoge.net server after which it was named. After activation on the device, the software collects information about it (IMEI, IMSI, memory, installed applications) and sends it to the server with ads and subsequently, regardless of the current activity, the user will see annoying ads on the device. Also, after collecting and sending information, the device with Kemoge receives in response from the server links to download ad applications and commands to remove original applications and fill the device with malicious code. Due to this, Kemoge is able to issue phishing pages in the process of paying for something with a bank card, stealing details and gaining access to the card. This 'pest' can affect relatively more devices in more than twenty countries around the world.
Summing up the review of this malware family, it is necessary to dwell on the rules that the user must follow in order to avoid infecting the device with one of the Trojans:
- Don't click on suspicious links in emails, text messages, websites and banner ads
- Do not install or prevent the automatic installation of third-party applications.
- Make sure that the device is updated to the latest official firmware version. Updates close known vulnerabilities, although they do not guarantee 100% protection.
- In some cases, constant use of a VPN is recommended
Mazar Bot
In the context of the topic of the material, one cannot fail to mention a new type of 'malware' discovered around the same time as GhostPush called Mazar Bot. Distribution takes place in a less sophisticated way – by link in SMS / MMS messages. Clicking on the link leads to downloading the application, through which the attack subsequently takes place. The application connects to the server and sends an SMS to the Iranian number in order to transmit the location of the device. Having gained access to a smartphone, attackers can control the device at will, send messages to premium numbers, read incoming messages (including payment authentication codes) and interrupt calls. But that's not all. Using the Polipo proxy protocol, criminals can carry out so-called middleman attacks (compromise of a communication channel by spoofing messages from one or both correspondents without their knowledge). On top of that, Mazar Bot is capable of embedding its code into Chrome, controlling device keys, activating sleep mode, and changing options in settings.
Mazar Bot code is extremely difficult to detect by antivirus (3/54 according to VirusTotal). This fact, coupled with the choice of methods of attacking devices, led to the popularity of the software, as evidenced by the sale of the corresponding code on several sites on the darknet. However, Mazar Bot has a strange feature: the software checks the device's regional affiliation and cancels the launch of the application if the device is of Russian 'origin'. Well, you can not be afraid, but certain thoughts suggest themselves. The protection methods from Mazar Bot are similar to the above.
Original materials: 1, 2, 3, 4, 5
Elir: cyber crime is gradually moving to a new level of interaction with potential victims, and we, as users, need to clearly understand how to behave on the network, what not to do and where not to look, to know enemies by sight. And if in the scenario of the 'evil family' one can sympathize with the users, the case with Mazar Bot raised a quite reasonable question: do people still use MMS? Yes, popular instant messengers are not distinguished by 100% protection of private information, but at least there is a chance that they will not miss such malicious links. I will repeat the thought expressed in one of the issues: our security in the network is a consequence of our actions, which may not always be correct and adequate. Be careful and follow simple rules.

